Creating the Stored Procedures
Requirement 1 dictates that only members of the Sensitive_high database role can execute INSERT and UPDATE methods on a table that contains columns with the sensitivity classification of "High". We have already established that the Borrower_Identification table contains one of these columns.
In addition, Requirement 2
dictates that all interaction with tables is to be performed through
views and stored procedures. Requirement 6 dictates that all data
modifications occur through stored procedures. In compliance with these
requirements we will create two stored procedures.
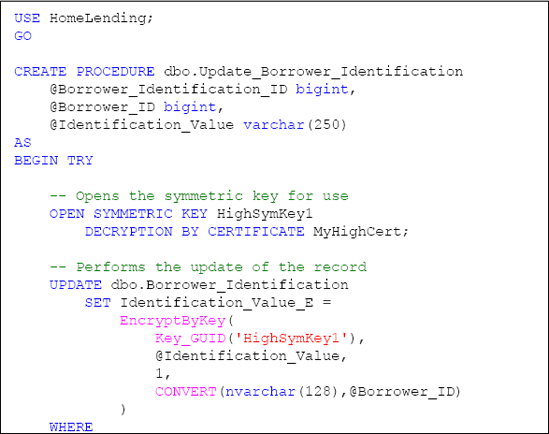
The first stored procedure, named Update_Borrower_Identification, will perform the following:
Open the HighSymKey1 symmetric key with the MyHighCert certificate through the OPEN SYMMETRIC KEY method.
Execute the UPDATE method while using the EncryptByKey method to encrypt the value that is passed in the @Identification_Value argument. This encryption includes the use of the @Borrower_ID argument as the authenticator.
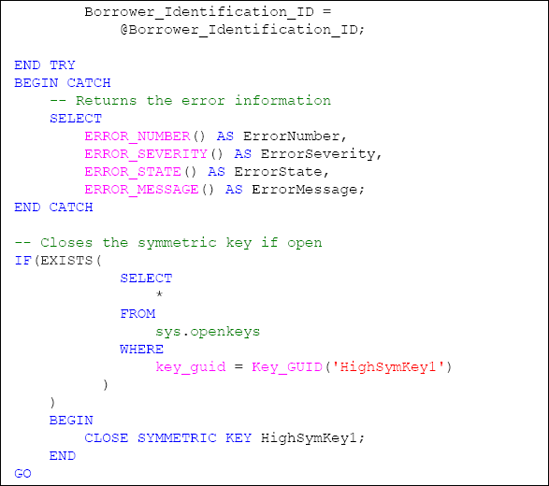
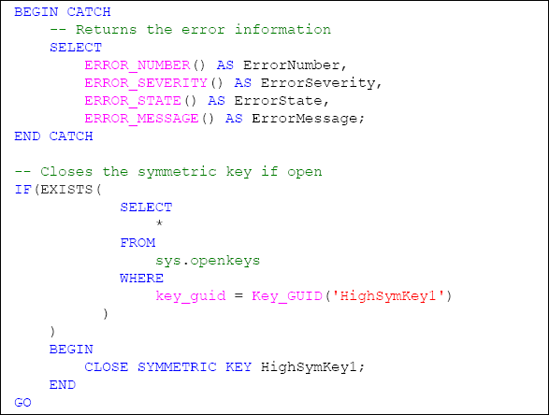
Catch the occurrence of an error so that the stored procedure fails gracefully. This is accomplished by the use of the TRY...CATCH method.
Check the HighSymKey1 symmetric key to determine if it is open before attempting to close it through the sys.openkeys catalog view. If it is open, the key is closed using the CLOSESYMMETRICKEY method.
Listing 4 shows the full code for the stored procedure.
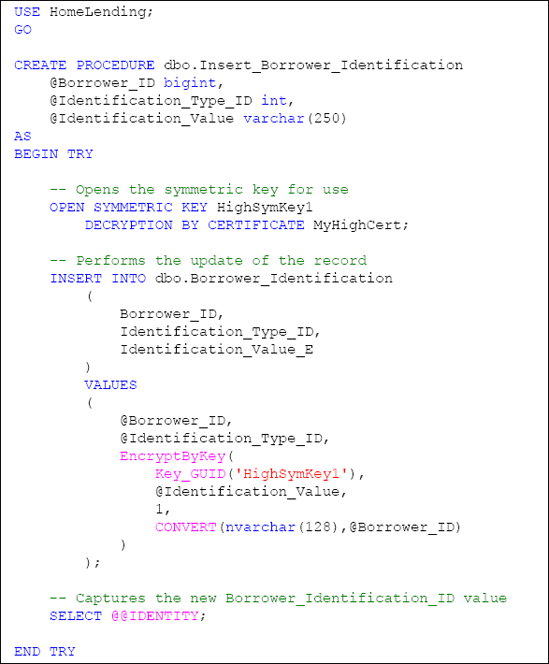
The second stored procedure, named Insert_Borrower_Identification, will perform the following:
Open the HighSymKey1 symmetric key with the MyHighCert certificate through the OPEN SYMMETRIC KEY method.
Execute the INSERT method while using the EncryptByKey method to encrypt the value that is passed in the @Identification_Value argument. This encryption includes the use of the @Borrower_ID argument as the authenticator.
Capture the new Borrower_Identification_ID of the inserted record, which is referenced through the use of @@IDENTITY, and returns it as the result of the stored procedure.
Catch the occurrence of an error so that the stored procedure fails gracefully. This is accomplished by the use of the TRY...CATCH method.
Check the HighSymKey1 symmetric key to determine if it is open before attempting to close it through the sys.openkeys catalog view. If it is open, the key is closed using the CLOSE SYMMETRIC KEY method.
Listing 5 shows the full code for the stored procedure.
The final step in implementing
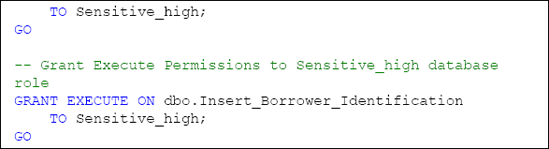
these stored procedures is to grant the appropriate permissions to them.
Requirement 6 allows the INSERT or UPDATE methods to be executed, if an encrypted column exists; only when the database role that performs the INSERT or UPDATE method has permissions granted to the key that performs the encryption.
The encrypted column in the Borrower_Information table, Information_Value_E, is encrypted by the HighSymKey1 symmetric key to which only the Sensitive_high database role has permissions to utilize; therefore, we will grant EXECUTE permissions to our two stored procedures only to the members of the Sensitive_high database role, as shown in Listing 6.